268
9.
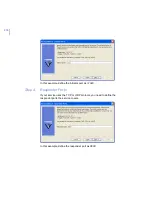
The first security level is now ready. Click
Add
to add the second
security level, in this example
Mobile
.
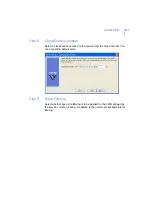
10. Enter the data in the cells by selecting a cell and clicking
Edit
. For the
Mobile
security level you should add the following data:
Priority:
The rules are checked in the order defined by the priority
numbers, starting from the smallest number.
Security Level: Enter the ID of the security level here; for
example: 20
mobile
.
Method 1
: Select
Dialup
from the drop-down list.
Argument 1
: You can leave this empty.
Method 2
: Select
Always
from the drop-down list.
Argument 2
: You can leave this empty.
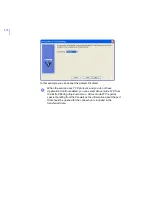
11. The configuration is now ready.
12. Click
to save the policy data.
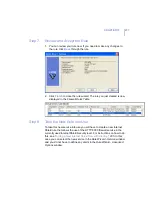
13. Click
to distribute the policy.
13.4
Troubleshooting Connection Problems
If there are connection problems, a host cannot access the Internet, and
you suspect that the Internet Shield might cause these problems, you can
use the following as a check list:
1.
Check that the computer is properly connected. Check that the
problem is not in the network cable.
2.
Check that ethernet is up and working properly.
Содержание CLIENT SECURITY 7.00
Страница 1: ...F Secure Client Security Administrator s Guide...
Страница 10: ...10 ABOUT THIS GUIDE Overview 11 Additional Documentation 13...
Страница 41: ...CHAPTER2 41 Click Next to continue...
Страница 44: ...44 Step 12 Review the changes that setup is about to make Click Start to start the installation...
Страница 75: ...CHAPTER3 75 Real Time Scanning Figure 3 10 Settings Real Time Scanning page...
Страница 78: ...78 Manual Scanning Figure 3 11 Settings Manual Scanning...
Страница 82: ...82 Spyware Control Figure 3 12 Settings Spyware Control...
Страница 88: ...88 Firewall Security Levels Figure 3 15 Settings Firewall Security Levels...
Страница 91: ...CHAPTER3 91 Firewall Rules Figure 3 16 Settings Firewall Rules...
Страница 135: ...CHAPTER4 135 Autoregistration Import Rules Figure 4 6 Import Autoregistered Hosts dialog Import Rules tab...
Страница 229: ...229 8 UPGRADING SOFTWARE Overview Upgrading Software 230...
Страница 278: ...278 A APPENDIX Modifying PRODSETT INI Overview 279 Configurable Prodsett ini Settings 279...
Страница 292: ...292 B APPENDIX E mail Scanning Alert and Error Messages Overview 293...
Страница 297: ...297 GLOSSARY...
Страница 310: ...310 Worm A computer program capable of replication by inserting copies of itself in networked computers...
Страница 311: ...311 Technical Support Overview 312 Web Club 312 Advanced Technical Support 312 F Secure Technical Product Training 313...