Exinda Network Orchestrator
3 Using
|
333
Where there are more than two appliances in a cluster, the interface for each appliance in a cluster must be con-
nected to a single, dedicated switch, such that each appliance can communicate with every other appliance without
requiring a route (they must be on the same Layer 2 LAN segment).
Example: Configure cluster through the CLI
Configuration using the CLI is very similar to that of the Web UI.
1.
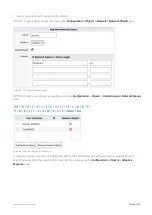
Configure a Cluster Internal address. Any interface not bound to a bridge or used in another role (e.g. Mirror or WCCP)
may be used. This command will need to be run on each node in the cluster, and each with a unique Cluster Internal
address.
(config) # cluster interface eth2
(config) # interface eth2 ip address 192.168.1.1 /24
2.
Configure the Cluster External IP. This command should be executed on all cluster nodes using the same Cluster
External IP
(config) # cluster master interface eth1
(config) # cluster master address vip 192.168.0.160 /24
3.
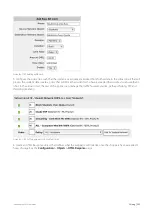
Enable the cluster.
(config) # cluster enable
NOTE
Configuration changes should only be made on the Cluster Master node. The role of the node currently logged into
will be displayed in the CLI prompt as shown below.
exinda-091cf4 [exinda-cluster: master] (config) #
4.
It is possible to view the status of all the members of a cluster from the CLI by issuing the following command.
(config)# show cluster global brief
Global cluster state summary
==============================
Cluster ID: exinda-default-cluster-id
Cluster name: exinda-cluster
Management IP: 192.168.0.160/24
Cluster master IF: eth1
Cluster node count: 2
ID Role State Host External Addr Internal Addr
-----------------------------------------------------------------
1* master online exinda-A 192.168.0.161 192.168.1.1
2 standby online exinda-B 192.168.0.162 192.168.1.2
3.5.6 Controlling anonymous proxy traffic
Users who want to bypass security policies that prevent tools from monitoring what they are doing, typically find an
open and anonymous HTTPS transparent proxy. They set their browsers to proxy all web requests through this
anonymous proxy. Those requests will be encrypted with https. The security tools cannot distinguish these transactions
from, say, a legitimate access to a financial website.
Содержание EXNV-10063
Страница 98: ...Exinda Network Orchestrator 2 Getting started 98 6 Click New The New Virtual Hard Disk wizard opens ...
Страница 99: ...Exinda Network Orchestrator 2 Getting started 99 7 Select VHDX as the Disk Format type and click Next ...
Страница 130: ...Exinda Network Orchestrator 2 Getting started 130 Screenshot 35 The life cycle of configuration status ...
Страница 369: ...Exinda Network Orchestrator 4 Settings 369 ...
Страница 411: ...Exinda Network Orchestrator 4 Settings 411 Screenshot 168 P2P OverflowVirtualCircuit ...
Страница 420: ...Exinda Network Orchestrator 4 Settings 420 Screenshot 175 Students OverflowVirtualCircuit ...
Страница 451: ...Exinda Network Orchestrator 4 Settings 451 ...