QX5
QXFXO4/QXISDN4/QXE1T1/QXFXS24; (SW Version 6.0.x)
95
QXFXO4/QXISDN4/QXE1T1/QXFXS24 Manual II: Administrator’s Guide
VPN Configuration
A
VPN (Virtual Private Network)
is established to connect two local networks (intranets) securely over the Internet securely. The VPN routers manage
authentication between servers and clients and handle data encryption for the connection. Only authorized users may access the network and the data
exchange cannot be intercepted.
VPN connections
are, in many ways, like every Internet connection, they are based on IP addresses, which means, the concerned VPN gateways must
authenticate the IP addresses of their respective partner’s VPN gateways. Each time a specific VPN is to be established, usually the same IP addresses are
expected. This will not create problems if both VPN partners have fixed WAN IP addresses. There may be circumstances reasons to prefer dynamically
allocated IP addresses. To enable devices that use a variable IP address as part of a VPN, they are turned into “Road Warriors”. For example, at this point
they are able to reach their corporate network via authentication at the company's VPN gateway device. This VPN gateway device must have a fixed IP
address for Internet access. Every VPN needs at least one VPN gateway with a fixed IP address.
The partner devices of a VPN must have different WAN IP addresses, and if they are connected to local area networks, these LAN’s must have different IP
addresses. As all QX gateway devices have the same default IP addresses on delivery, at least one of them must be reconfigured in order to set a new IP
address.
QX gateway supports several kinds of VPN connections such as
IPSec
and
PPTP/L2TP
.
Attention:
It is strongly recommended not to run different types of VPN tunnels between the same endpoints simultaneously.
IPSec Configuration
An IPSec connection includes authentication and encryption to protect data integrity and confidentiality. VPNs are “virtual” in the sense that individuals
can use the public Internet as a means of securely accessing an internal network. Once the IPSec connection is established, users have access to the same
network resources, addresses, and so forth as if they were connected locally. VPNs are “private” because the data is encrypted between two VPN gateways.
Encryption makes it very difficult for anyone to intercept data and capture sensitive information such as passwords. The QX gateway can be set up to act
as a VPN router when connected to the Internet with a fixed IP address or as an IPSec connection Road Warrior when using dynamic IP addresses.
Establishing an IPSec connection normally requires the functionality of a VPN gateway on each side of the communication line. An intelligent Internet
access router, for example QX gateway, delivers this function but also PCs or workstations may also be equipped with VPN gateway functionality. Home
offices typically prefer dynamically allocated IP addresses.
When QX gateway is connected to the Internet with a fixed IP address, it will be set up to act as a VPN gateway. QX gateway is then prepared to establish
an IPSec connection with another VPN gateway device, but also allows access to Road Warriors. A notebook /laptop used by a traveling employee could
also be a Road Warrior. Access to their company’s intranet via an IPSec connection can be obtained regardless of their location.
QX gateway can also be set up to act as a Road Warrior. If a home office is connected to the Internet via QX gateway with PPPoE (Point-to-Point Protocol)
and dynamic IP addressing, setting up QX gateway as a Road Warrior will allow an IPSec connection to the corporate network.
For the encryption and decryption of the data transmitted via the IPSec connection, a key is used.
RSA
used by QX gateway is an asymmetric key system. It
has to be available on both sides of the IPSec connection and will generate a different pair of keys on each side, a private key and a public key. During the
connection establishment, some data is encrypted with the remote party’s public key. They can be decrypting the data with their private key and the data
encrypted there with QX gateway’s public key can be decrypted with QX gateway’s private key. Since the private key is never transmitted, it stays
completely unknown to everyone, thus the system remains safe. Even if someone gets the public key, decryption cannot be possible without the private
key. QX IP PBX generates such a pair of keys automatically when it is set up. The user cannot see the private key, but must know the public key because
their IPSec connection partner will need it.
Please Note:
A pair of keys will always be generated, a public one and a private one. The previously generated pair of keys will become invalid as well as
all existing IPSec connections that use RSA keying.
The
IPSec Configuration
link refers to the page where IPSec connections can be created and managed.
The
IPSec Configuration
page consists of two sub-pages:
Connection
and
RSA Key Management
.
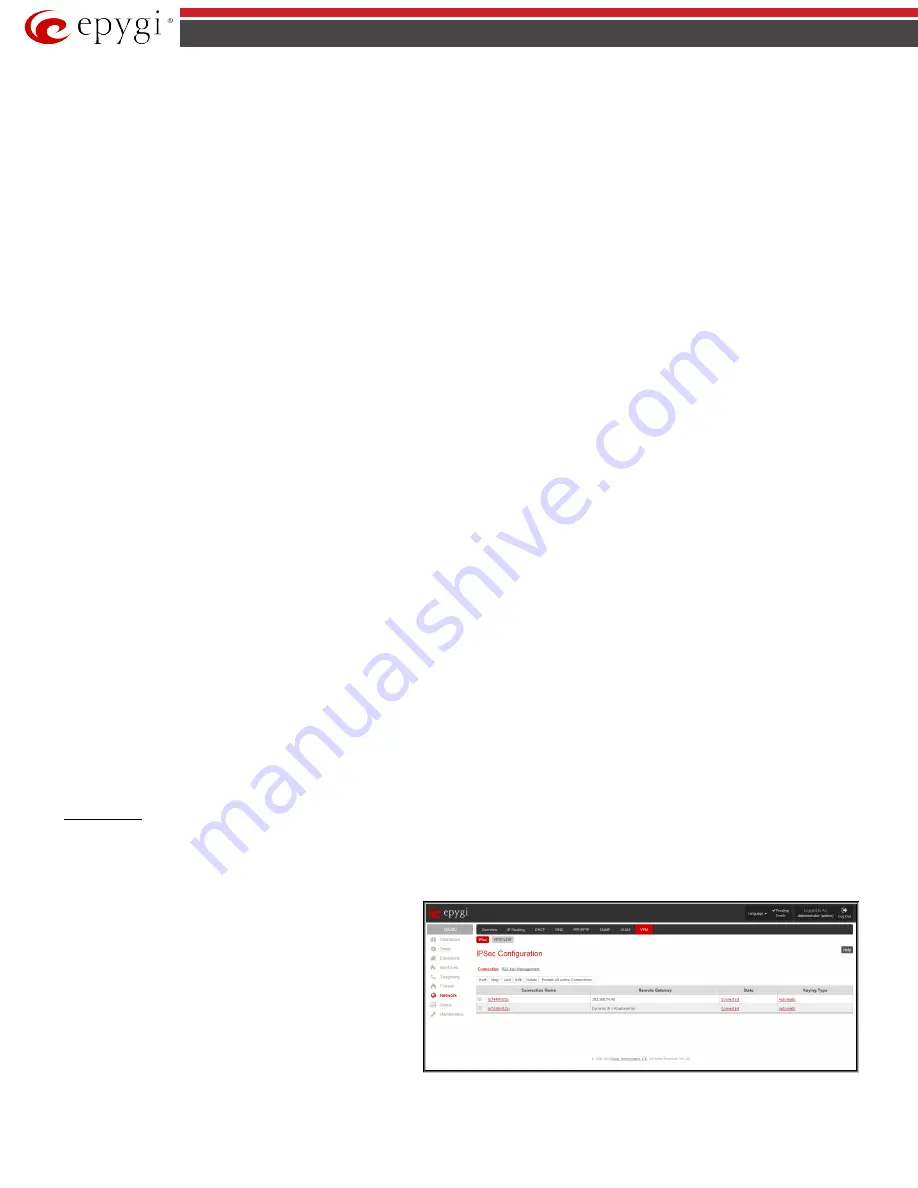
Connection
The Connection sub-page provides an overview of all existing IPSec connections characterized by their
Connection Name
, the
Remote Gateway
(the IP
address or the hostname of the IPSec connection partner), the
State
of the IPSec connection (Stopped, Connecting, Activated, Waiting or Connected) and
the dedicated
Keying Type
(the encryption type). The content of the table can be sorted in ascending or descending order by clicking on the header of the
respective column. There is a checkbox for every IPSec connection to select it for further editing.
Start
activates the connection establishment of the selected IPSec
connection. The
State
of the IPSec connection will change into
“Connected” or “Activated” depending on the IPSec connection
type. If no record is selected, the error message “One Record
should be selected” appears.
Attention:
It is not recommended to simultaneously start a static
and a dynamic connection configured to use the same secret key. A
dynamic connection may capture the static connection peer and
vice versa, depending on which connection established first.
Stop
disconnects the selected IPSec connection. The state of the
IPSec connection will change into “Stopped”. If no record is
selected, the error message “One Record should be selected” will
appear. More than one record may be selected at a time to be
Fig.II- 145: IPSec Configuration - Connection Settings page
















































