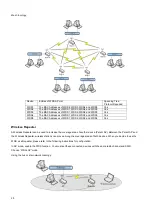
36
WPA Authentication Mode
The WPA feature provides a high level of assurance for end-users and administrators that their data will remain private and
that access to their network is restricted to authorized users. You can choose the WPA encryption and select the
Authentication Mode. This device supports two WPA modes:
Enterprise (RADIUS)
In this mode authentication is achieved via a WPA RADIUS Server. You need a RADIUS or other authentication server on the
network. When WPA Authentication mode is Enterprise (RADIUS), you have to add user accounts and the target device to the
RADIUS Server. In the device, you need to specify the IP address Password (Shared Secret) and Port number of the target
RADIUS server.
Pre-Share Key
In this mode you can use the Pre-shared Key to enhance your security setting. This mode requires only an access point and
client station that supports WPA-PSK. The WPA-PSK settings include Key Format, Length and Value. They must be the same
as each wireless client in your wireless network. When the Key format is Passphrase, the key value should have 8~63 ACSII
chars. When Key format is Hex, the key value should have 64 hexadecimal digits (0~9, a~f or A~F).
Содержание DLB70XX
Страница 1: ...DLB70XX WLAN Dual Outdoor Radio User Manual Version 1 0 0 11 08 2006 ...
Страница 28: ...27 ...
Страница 40: ...39 ...
Страница 47: ...46 Clone MAC address for Static IP WAN access type Clone MAC address for PPPoE WAN access type ...
Страница 48: ...47 Clone MAC address for PPTP WAN access type Physical LAN interface MAC address clone ...
Страница 51: ...50 In the Dynamic Routing Table there are two routings for Network 3 and Network 4 ...
Страница 55: ...54 Configuring VPN ...
Страница 66: ...65 ...