•
Networks that require resource accounting. You can use RADIUS accounting independently of RADIUS
authentication or authorization. The RADIUS accounting functions allow data to be sent at the start and
end of services, showing the amount of resources (such as time, packets, bytes, and so forth) used during
the session. An Internet service provider might use a freeware-based version of RADIUS access control
and accounting software to meet special security and billing needs.
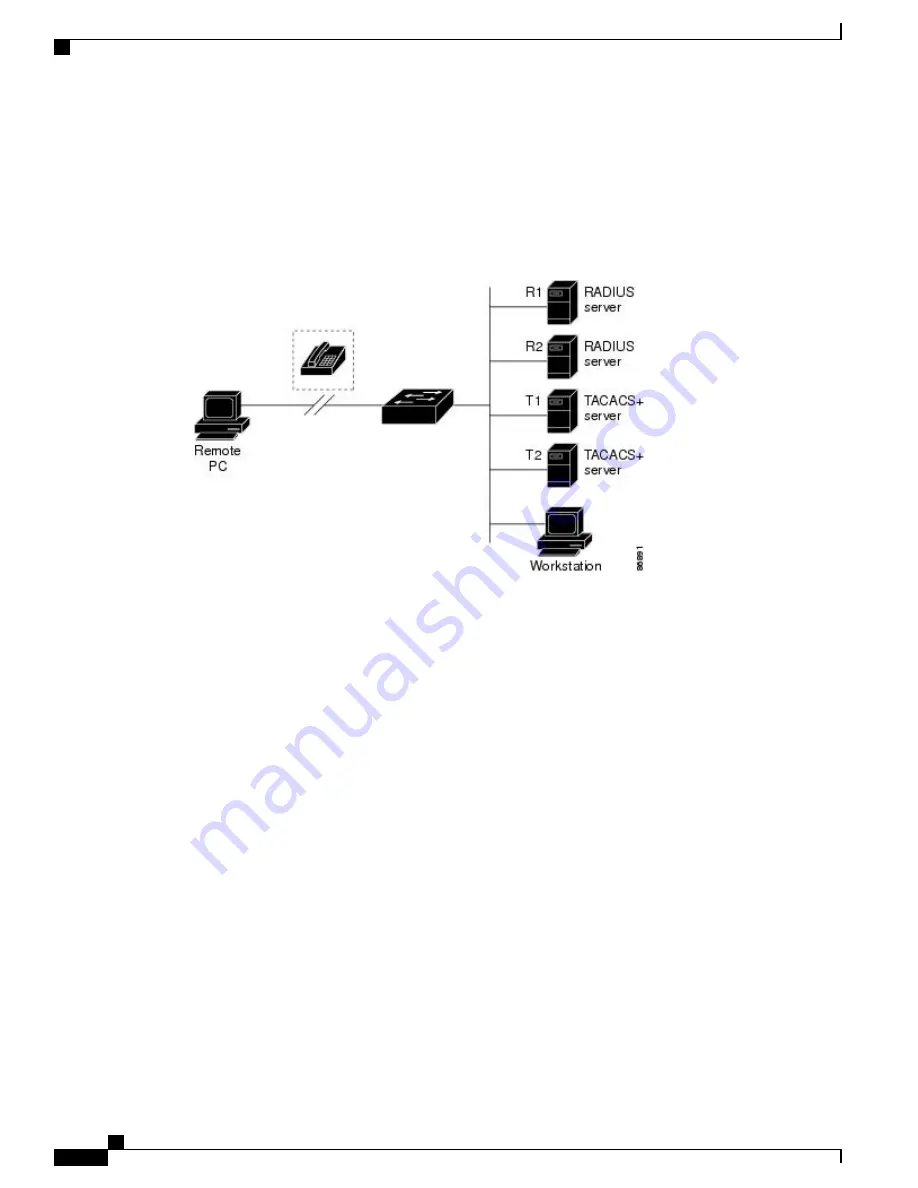
Figure 2: Transitioning from RADIUS to Services
Related Topics
Restrictions for Controlling Switch Access with RADIUS, on page 52
RADIUS Operation
When a user attempts to log in and authenticate to a switch that is access controlled by a RADIUS server,
these events occur:
1
The user is prompted to enter a username and password.
2
The username and encrypted password are sent over the network to the RADIUS server.
3
The user receives one of the following responses from the RADIUS server:
•
ACCEPT
—
The user is authenticated.
•
REJECT
—
The user is either not authenticated and is prompted to re-enter the username and password,
or access is denied.
•
CHALLENGE
—
A challenge requires additional data from the user.
•
CHALLENGE PASSWORD
—
A response requests the user to select a new password.
The ACCEPT or REJECT response is bundled with additional data that is used for privileged EXEC or
network authorization. The additional data included with the ACCEPT or REJECT packets includes these
items:
Catalyst 2960-XR Switch Security Configuration Guide, Cisco IOS Release 15.0(2)EX1
54
OL-29434-01
Configuring RADIUS
RADIUS Operation






























