17-18
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 17 ASA CX Module
Configure the ASA CX Module
Example:
hostname(config)# policy-map global_policy
In the default configuration, the global_policy policy map is assigned globally to all interfaces. If you
want to edit the global_policy, enter global_policy as the policy name.
Step 3
Identify the class map you created at the start of this procedure.
class
name
Example:
hostname(config-pmap)# class cx_class
Step 4
Send the traffic to the ASA CX module.
cxsc
{
fail-close
|
fail-open
} [
auth-proxy
|
monitor-only
]
Where:
•
The
fail-close
keyword sets the ASA to block all traffic if the ASA CX module is unavailable.
•
The
fail-open
keyword sets the ASA to allow all traffic through, uninspected, if the module is
unavailable.
•
The optional
auth-proxy
keyword enables the authentication proxy, which is required for active
authentication.
•
For demonstration purposes only, specify
monitor-only
to send a read-only copy of traffic to the
ASA CX module. You must configure all classes and policies to be either in monitor-only mode, or
in normal inline mode; you cannot mix both modes on the same ASA.
Example:
hostname(config-pmap-c)# cxsc fail-close auth-proxy
Step 5
If you created multiple class maps for ASA CX traffic, you can specify another class for the policy and
apply the
cxsc
redirect action.
Feature Matching Within a Service Policy, page 1-5
for detailed information about how the order of
classes matters within a policy map. Traffic cannot match more than one class map for the same action
type.
Step 6
If you are editing an existing service policy (such as the default global policy called global_policy), you
are done. Otherwise, activate the policy map on one or more interfaces.
service-policy
policymap_name
{
global
|
interface
interface_name
}
Example:
hostname(config)# service-policy global_policy global
The
global
keyword applies the policy map to all interfaces, and
interface
applies the policy to one
interface. Only one global policy is allowed. You can override the global policy on an interface by
applying a service policy to that interface. You can only apply one policy map to each interface.
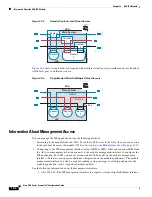
Configure Traffic-Forwarding Interfaces (Monitor-Only Mode)
For demonstration purposes only, you can configure traffic-forwarding interfaces, where all traffic is
forwarded directly to the ASA CX module. For normal ASA CX operation, see
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...