11-8
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 11 Service Policy Using the Modular Policy Framework
Guidelines for Service Policies
Feature Matching for Multiple Service Policies
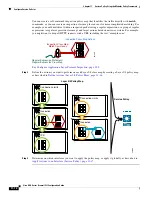
For TCP and UDP traffic (and ICMP when you enable stateful ICMP inspection), service policies
operate on traffic flows, and not just individual packets. If traffic is part of an existing connection that
matches a feature in a policy on one interface, that traffic flow cannot also match the same feature in a
policy on another interface; only the first policy is used.
For example, if HTTP traffic matches a policy on the inside interface to inspect HTTP traffic, and you
have a separate policy on the outside interface for HTTP inspection, then that traffic is not also inspected
on the egress of the outside interface. Similarly, the return traffic for that connection will not be
inspected by the ingress policy of the outside interface, nor by the egress policy of the inside interface.
For traffic that is not treated as a flow, for example ICMP when you do not enable stateful ICMP
inspection, returning traffic can match a different policy map on the returning interface. For example, if
you configure IPS on the inside and outside interfaces, but the inside policy uses virtual sensor 1 while
the outside policy uses virtual sensor 2, then a non-stateful Ping will match virtual sensor 1 outbound,
but will match virtual sensor 2 inbound.
Guidelines for Service Policies
IPv6 Guidelines
Supports IPv6 for the following features:
•
Application inspection for DNS, FTP, HTTP, ICMP, ScanSafe, SIP, SMTP, IPsec-pass-thru, and
IPv6.
•
ASA IPS
•
ASA CX
•
ASA FirePOWER
•
NetFlow Secure Event Logging filtering
•
TCP and UDP connection limits and timeouts, TCP sequence number randomization
•
TCP normalization
•
TCP state bypass
•
User statistics for Identity Firewall
Class Map (Traffic Class) Guidelines
The maximum number of class maps (traffic classes) of all types is 255 in single mode or per context in
multiple mode. Class maps include the following types:
•
Layer 3/4 class maps (for through traffic and management traffic).
•
Inspection class maps
•
Regular expression class maps
•
match
commands used directly underneath an inspection policy map
This limit also includes default class maps of all types, limiting user-configured class maps to
approximately 235. See
Default Class Maps (Traffic Classes), page 11-10
Policy Map Guidelines
See the following guidelines for using policy maps:
Содержание ASA 5508-X
Страница 11: ...P A R T 1 Access Control ...
Страница 12: ......
Страница 60: ...4 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 4 Access Rules History for Access Rules ...
Страница 157: ...P A R T 2 Network Address Translation ...
Страница 158: ......
Страница 204: ...9 46 Cisco ASA Series Firewall CLI Configuration Guide Chapter 9 Network Address Translation NAT History for NAT ...
Страница 232: ...10 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 10 NAT Examples and Reference DNS and NAT ...
Страница 233: ...P A R T 3 Service Policies and Application Inspection ...
Страница 234: ......
Страница 379: ...P A R T 4 Connection Management and Threat Detection ...
Страница 380: ......
Страница 400: ...16 20 Cisco ASA Series Firewall CLI Configuration Guide Chapter 16 Connection Settings History for Connection Settings ...
Страница 414: ...17 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 Quality of Service History for QoS ...