Chapter 10 Interfaces
UAG Series User’s Guide
165
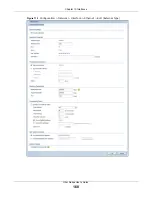
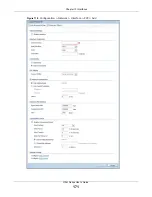
10.3.2 Object References
When a configuration screen includes an
Object Reference
icon, select a configuration object and
click
Object Reference
to open the
Object Reference
screen. This screen displays which
configuration settings reference the selected object. The fields shown vary with the type of object.
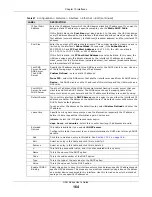
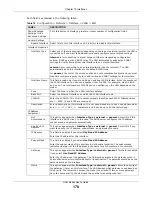
Enable Logs for
IP/MAC Binding
Violation
Select this option to have the UAG generate a log if a device connected to this interface
attempts to use an IP address that is bound to another device’s MAC address.
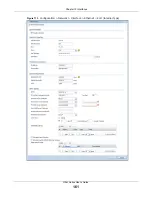
Static DHCP
Table
Configure a list of static IP addresses the UAG assigns to computers connected to the
interface. Otherwise, the UAG assigns an IP address dynamically using the interface’s
IP Pool Start Address
and
Pool Size
.
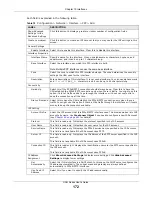
Add
Click this to create a new entry.
Edit
Select an entry and click this to be able to modify it.
Remove
Select an entry and click this to delete it.
#
This field is a sequential value, and it is not associated with a specific entry.
IP Address
Enter the IP address to assign to a device with this entry’s MAC address.
MAC
Enter the MAC address to which to assign this entry’s IP address.
Description
Enter a description to help identify this static DHCP entry. You can use alphanumeric
and
()+/:=?!*#@$_%-
characters, and it can be up to 60 characters long.
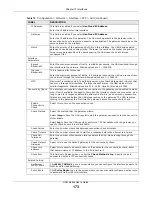
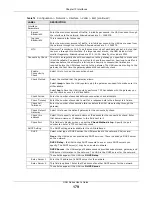
MAC Address
Setting
This section appears when
Interface Type
is
external
or
general
. Have the interface
use either the factory assigned default MAC address, a manually specified MAC address,
or clone the MAC address of another device or computer.
Use Default MAC
Address
Select this option to have the interface use the factory assigned default MAC address.
By default, the UAG uses the factory assigned MAC address to identify itself.
Overwrite
Default MAC
Address
Select this option to have the interface use a different MAC address. Either enter the
MAC address in the fields or click
Clone by host
and enter the IP address of the device
or computer whose MAC you are cloning. Once it is successfully configured, the address
will be copied to the configuration file. It will not change unless you change the setting
or upload a different configuration file.
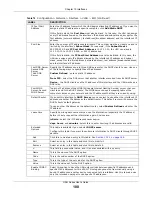
Related Setting
Configure
PPPoE/PPTP
Click
PPPoE/PPTP
if this interface’s Internet connection uses PPPoE or PPTP.
Configure WAN
TRUNK
Click
WAN TRUNK
to go to a screen where you can set this interface to be part of a
WAN trunk for load balancing.
This field appears when
Interface Type
is
general
.
Configure Policy
Route
Click
Policy Route
to go to the policy route summary screen where you can manually
associate traffic with this interface.
You must manually configure a policy route to add routing and SNAT settings for an
interface with the
Interface Type
set to
general
. You can also configure a policy route
to override the default routing and SNAT behavior for an interface with an
Interface
Type
of
internal
or
external
.
OK
Click
OK
to save your changes back to the UAG.
Cancel
Click
Cancel
to exit this screen without saving.
Table 67
Configuration > Network > Interface > Ethernet > Edit (continued)
LABEL
DESCRIPTION