P-660H/HW-T Series User’ Guide
Appendix K
412
For added security, certificate-based authentications (EAP-TLS, EAP-TTLS and PEAP) use
dynamic keys for data encryption. They are often deployed in corporate environments, but for
public deployment, a simple user name and password pair is more practical. The following
table is a comparison of the features of authentication types.
WPA
User Authentication
WPA applies IEEE 802.1x and Extensible Authentication Protocol (EAP) to authenticate
wireless stations using an external RADIUS database.
Encryption
WPA improves data encryption by using Temporal Key Integrity Protocol (TKIP) or
Advanced Encryption Standard (AES), Message Integrity Check (MIC) and IEEE 802.1x.
TKIP uses 128-bit keys that are dynamically generated and distributed by the authentication
server. It includes a per-packet key mixing function, a Message Integrity Check (MIC) named
Michael, an extended initialization vector (IV) with sequencing rules, and a re-keying
mechanism.
TKIP regularly changes and rotates the encryption keys so that the same encryption key is
never used twice.
The RADIUS server distributes a Pairwise Master Key (PMK) key to the AP that then sets up
a key hierarchy and management system, using the PMK to dynamically generate unique data
encryption keys to encrypt every data packet that is wirelessly communicated between the AP
and the wireless stations. This all happens in the background automatically.
AES (Advanced Encryption Standard) also uses a secret key. This implementation of AES
applies a 128-bit key to 128-bit blocks of data.
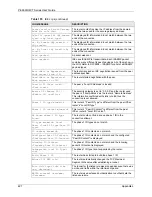
Table 141
Comparison of EAP Authentication Types
EAP-MD5
EAP-TLS
EAP-TTLS
PEAP
LEAP
Mutual Authentication
No
Yes
Yes
Yes
Yes
Certificate – Client
No
Yes
Optional
Optional
No
Certificate – Server
No
Yes
Yes
Yes
No
Dynamic Key Exchange
No
Yes
Yes
Yes
Yes
Credential Integrity
None
Strong
Strong
Strong
Moderate
Deployment Difficulty
Easy
Hard
Moderate
Moderate
Moderate
Client Identity Protection
No
No
Yes
Yes
No
Summary of Contents for P-660H Series
Page 2: ......
Page 10: ...P 660H HW T Series User Guide 9 Customer Support ...
Page 32: ...P 660H HW T Series User Guide 31 List of Figures ...
Page 38: ...P 660H HW T Series User Guide 37 List of Tables ...
Page 42: ...P 660H HW T Series User Guide 41 Introduction to DSL ...
Page 62: ...P 660H HW T Series User Guide 61 Chapter 3 Wizard Setup for Internet Access ...
Page 90: ...P 660H HW T Series User Guide 89 Chapter 5 Wireless LAN ...
Page 132: ...P 660H HW T Series User Guide 131 Chapter 10 Firewalls ...
Page 162: ...P 660H HW T Series User Guide 161 Chapter 13 Remote Management Configuration ...
Page 176: ...P 660H HW T Series User Guide 175 Chapter 14 Universal Plug and Play UPnP ...
Page 182: ...P 660H HW T Series User Guide 181 Chapter 15 Logs Screens ...
Page 196: ...P 660H HW T Series User Guide 195 Chapter 16 Media Bandwidth Management Advanced Setup ...
Page 208: ...P 660H HW T Series User Guide 207 Chapter 17 Maintenance ...
Page 218: ...P 660H HW T Series User Guide 217 Chapter 19 Menu 1 General Setup ...
Page 222: ...P 660H HW T Series User Guide 221 Chapter 20 Menu 2 WAN Backup Setup ...
Page 226: ...P 660H HW T Series User Guide 225 Chapter 21 Menu 3 LAN Setup ...
Page 230: ...P 660H HW T Series User Guide 229 Chapter 22 Wireless LAN Setup ...
Page 236: ...P 660H HW T Series User Guide 235 Chapter 23 Internet Access ...
Page 250: ...P 660H HW T Series User Guide 249 Chapter 25 Static Route Setup ...
Page 254: ...P 660H HW T Series User Guide 253 Chapter 26 Bridging Setup ...
Page 270: ...P 660H HW T Series User Guide 269 Chapter 27 Network Address Translation NAT ...
Page 286: ...P 660H HW T Series User Guide 285 Chapter 29 Filter Configuration ...
Page 306: ...P 660H HW T Series User Guide 305 Chapter 32 System Information and Diagnosis ...
Page 318: ...P 660H HW T Series User Guide 317 Chapter 33 Firmware and Configuration File Maintenance ...
Page 324: ...P 660H HW T Series User Guide 323 Chapter 34 System Maintenance ...
Page 328: ...P 660H HW T Series User Guide 327 Chapter 35 Remote Management ...
Page 338: ...P 660H HW T Series User Guide 337 Chapter 36 IP Policy Routing ...
Page 342: ...P 660H HW T Series User Guide 341 Chapter 37 Call Scheduling ...
Page 358: ...P 660H HW T Series User Guide 357 Appendix A ...
Page 360: ...P 660H HW T Series User Guide 359 Appendix B ...
Page 384: ...P 660H HW T Series User Guide 383 Appendix D ...
Page 388: ...P 660H HW T Series User Guide 387 Appendix F ...
Page 394: ...P 660H HW T Series User Guide 393 Appendix G ...
Page 398: ...P 660H HW T Series User Guide 397 Appendix H ...
Page 401: ...P 660H HW T Series User Guide Appendix I 400 ...
Page 402: ...P 660H HW T Series User Guide 401 Appendix I ...
Page 456: ...P 660H HW T Series User Guide 455 Appendix M ...