_______________________________________________________________________________________________________
_______________________________________________________________________________________________________
© Virtual Access 2018
GW2020 Series User Manual
Issue: 2.1
Page 300 of 423
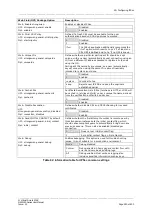
option remotelan '172.19.101.3'
option remotelanmask '255.255.255.255'
option authby 'xauthpsk'
option xauth_identity 'testxauth'
option ike '3des-md5-modp1024'
option esp '3des-md5'
option waniface 'wan'
option inherit_child ‘0’
option initial_contact ‘0’
29.3.3
Shunt connection
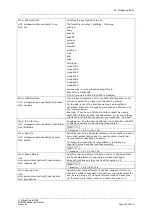
If the remote LAN network is 0.0.0.0/0 then all traffic generated on the local LAN will be
sent via the IPSec tunnel. This includes the traffic destined to the router’s IP address. To
avoid this situation you must include an additional config connection section.
# Commands
touch /etc/config/strongswan
uci add strongswan connection
uci set strongswan.@connection[1].name=local
uci set strongswan.@connection[1].enabled=yes
uci set strongswan.@connection[1].locallan=10.1.1.1
uci set strongswan.@connection[1].locallanmask=255.255.255.255
uci set strongswan.@connection[1].remotelan=10.1.1.0
uci set strongswan.@connection[1].remotelanmask=255.255.255.0
uci set strongswan.@connection[1].type=pass
uci set strongswan.@connection[1].auto=route
uci commit
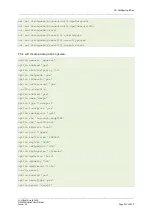
This will create the following output:
config connection
option name 'local'
option enabled 'yes'
option locallan '10.1.1.1'
option locallanmask '255.255.255.255'
option remotelan '10.1.1.0'
option remotelanmask '255.255.255.0'
option type 'pass'
option auto 'route'