_______________________________________________________________________________________________________
_______________________________________________________________________________________________________
© Virtual Access 2018
GW2020 Series User Manual
Issue: 2.1
Page 280 of 423
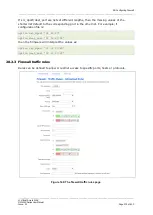
28.3.5.1
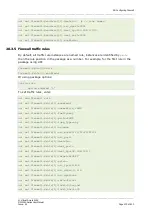
Custom firewall scripts: includes
It is possible to include custom firewall scripts by specifying one or more include sections
in the firewall configuration.
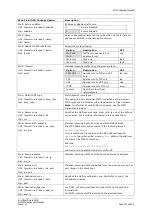
There is only one possible parameter for includes:
Parameter
Description
path
Specifies a shell script to execute on boot or firewall restarts.
Custom scripts are executed as shell scripts and are expected to contain iptables
commands.
28.4
IPv6 notes
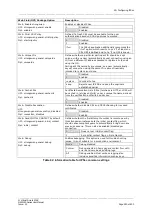
As described above, the option family is used for distinguishing between IPv4, IPv6 and
both protocols. However, the family is inferred automatically if a specific IP address
family is used. For example; if IPv6 addresses are used then the rule is automatically
treated as IPv6 only rule.
config rule
option src wan
option src_ip fdca:f00:ba3::/64
option target ACCEPT
Similarly, the following rule is automatically treated as IPv4 only.
config rule
option src wan
option dest_ip 88.77.66.55
option target REJECT
Rules without IP addresses are automatically added to iptables and ip6tables, unless
overridden by the family option. Redirect rules (port forwards) are always IPv4 since
there is no IPv6 DNAT support at present.
28.5
Implications of DROP vs. REJECT
The decision whether to drop or to reject traffic should be done on a case-by-case basis.
Many people see dropping traffic as a security advantage over rejecting it because it
exposes less information to a hypothetical attacker. While dropping slightly increases
security, it can also complicate the debugging of network issues or cause unwanted side-
effects on client programs.
If traffic is rejected, the router will respond with an icmp error message ("destination
port unreachable") causing the connection attempt to fail immediately. This also means
that for each connection attempt a certain amount of response traffic is generated. This
can actually harm if the firewall is attacked with many simultaneous connection
attempts, the resulting backfire of icmp responses can clog up all available upload and
make the connection unusable (DoS).