aXsGUARD Identifier 3.0.2.0 Product Guide v1.5
Policies
20
Policies
20.1
Overview
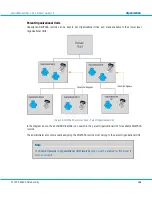
Policies specify various settings that affect all request handling processes. Each request is handled according to a
Policy identified by the applicable client and server records (see also sections
components respectively).
Policy records can be edited, copied or deleted using the Administration Web Interface (see section
Administration Interfaces).
In this section, we explain policy properties. In addition we explain the concept of policy inheritance and provide
example settings for the aXsGUARD Identifier RADIUS Self-Assignment Policy.
We strongly recommend that you read section
first, to better understand how policies influence the
authentication process.
20.2
Policy Properties
There are many policy settings which can be defined through the Administration Web Interface:
General Policy settings, such as:
whether local authentication requires an OTP generated from a DIGIPASS device, or whether a password (or
both) is required (see section
whether back-end authentication is to be used (never, always or if needed), and if so the back-end protocol,
e.g. RADIUS, Novel e-directory or Microsoft Active Directory (see section
User Policy settings, such as whether Dynamic User Registration is permitted, Password Autolearn and Stored
Password Proxy (see sections
DIGIPASS Policy settings, such as whether Auto- or Self-Assignment is possible and the Grace Period (see
Application settings for 1- and 2-step Challenge/Response authentication and for Virtual and Backup Virtual
DIGIPASS (see section
Some Policy properties can be overruled in User or DIGIPASS records (see sections
and
). Please refer to the
aXsGUARD Identifier Administrator's Reference Guide
for a full listing of the fields available for configuring policies.
©
2009 VASCO Data Security
121