Personal aXsGUARD - 7.7.1
Chapter 3. Features and Concepts
© VASCO Data Security 2013
7
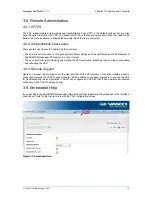
• PAX Network settings, such as routing, NAT and DNS servers.
• PAX DHCP server settings.
• Wireless Access settings, in case you are connecting to the PAX from a PC equipped with a wireless network
device.
• Firewall Policies which regulate traffic through the VPN tunnel, as well as traffic towards the Internet.
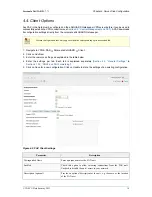
3.3. Security Recommendations
There are two possible firewall scenarios:
• The VPN connection is up: the aXsGUARD Gatekeeper pushes the configured Firewall policies onto the
PAX. These policies regulate traffic from the PAX’s LAN towards the Internet, as well as traffic going through
the VPN tunnel (towards or through the aXsGUARD Gatekeeper). The system default Firewall policies only
accept ICMP traffic and VASCO remote support connections.
• The VPN connection is down: the PAX protects your network from incoming connections. In this state,
the PAX behaves like a home network router. All traffic towards the Internet is allowed, traffic coming from
the Internet is dropped, except ICMP traffic and VASCO remote support connections.
Figure 3.2. PAX Firewall Scenarios
The stat-sec Firewall Policy and dynamic policies configured for PPTP, L2TP or OpenVPN do not
apply to the PAX. All PAX Firewall rights must be configured separately on the corporate aXsGUARD
Gatekeeper. The PAX downloads its Firewall configuration when it connects to the aXsGUARD
Gatekeeper VPN server. Configure the Firewall settings as explained below.
• Restrict Firewall Access of the PAX to the corporate network resources which are specifically needed by
the client(s). This improves security in case a client is hijacked or compromised, e.g. if a client is infected
with a trojan virus.
• The pre-configured aXsGUARD Gatekeeper Firewall policy (fwd-access-lan) can be used to provide the
appropriate security for VPN clients and for system administrators who do no wish to configure their own
Firewall Policies. However, we strongly encourage system administrators to implement their own Firewall
Policies, install a client-side firewall and anti-malware software.
• VASCO recommends a setup where potentially dangerous or infected client computers connect directly to
the Internet using an existing installation. Only computers that need remote access to the corporate LAN