51
Becoming familiar with the SGMI
Working with configurations of objects
■
Select the object, and then on the Edit menu, click
Properties
.
Properties dialog boxes have two or more tabs:
■
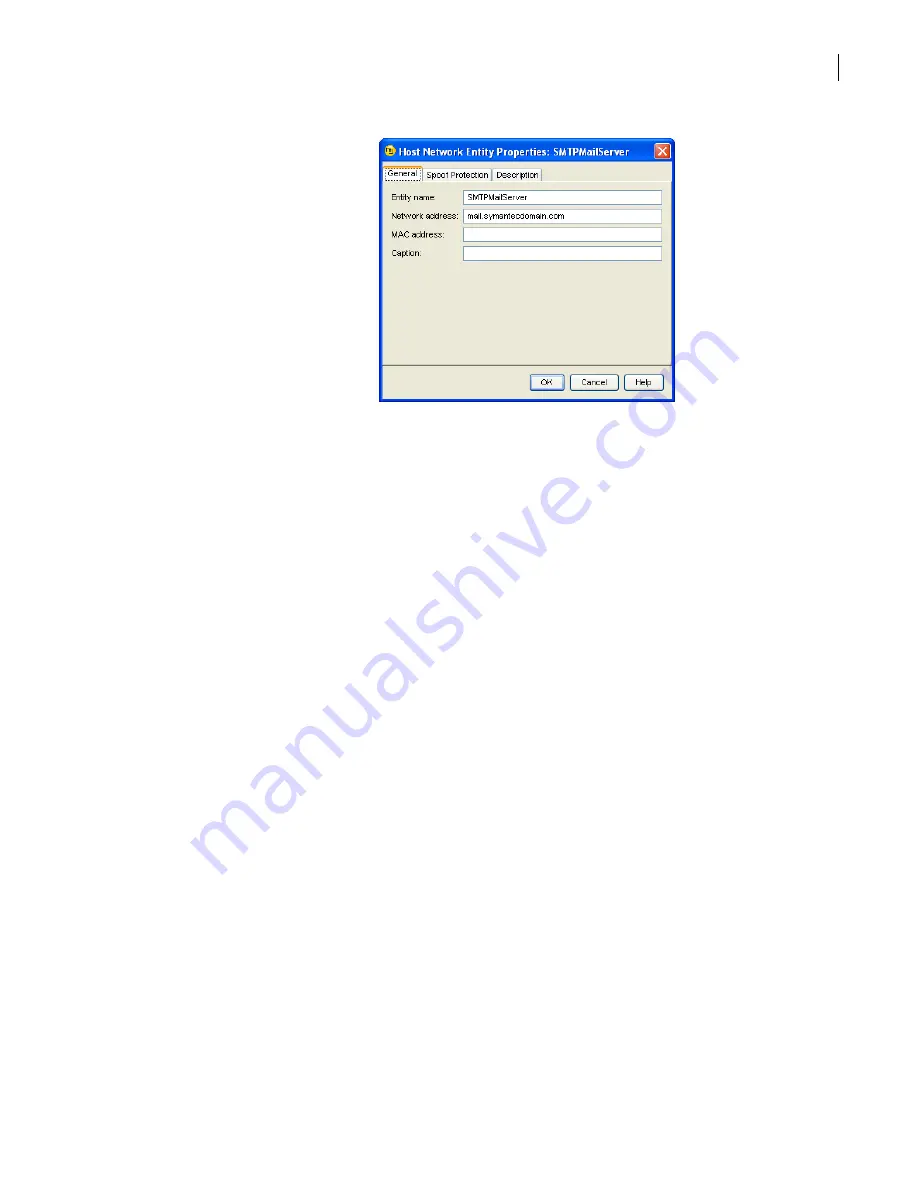
The General tab shows whether the object is enabled and displays its name and a short
caption describing the object.
It may include other information, such as the IP address and MAC Address in this example.
When an object does not have many configurable properties, the General tab may contain all
of the properties.
■
Other tabs may describe additional properties of the object.
■
The Description tab can contain a more detailed description.
For example, you can use the Description tab to record who makes configuration changes or
when they are made. You can then use these details as filter criteria when searching for
objects.
2
Click each tab to view additional property details.
Modifying the properties of an object
As your security needs change, you will need to modify the configuration objects that represent your
security environment.
To modify the properties of an object
1
In the SGMI, in the right pane, select the object that you want to modify.
2
Since objects in the SGMI can be used together, before you modify an object it is strongly
recommended that you check where it is used. Do the following:
■
To initiate a check, in the View menu, click
In use by
.
A window opens at the bottom of the SGMI, showing a search for objects that use the one you
want to modify.
■
To close the window, click the
X
icon in the upper left corner of the bottom window.
3
To modify the object, double-click it in the table.
4
In the object’s properties dialog box, use the tabs to navigate to the property that you want to
change.
5
Make the desired or required changes, and then click
OK
.
In the table, a blue ball appears to the left of the object, indicating that it has been modified.
Summary of Contents for Security 5600 Series, Security 5400 Series,Clientless VPN 4400 Series
Page 76: ...76 Managing administrative access Enabling SSH for command line access to the appliance...
Page 242: ...242 Defining your security environment Controlling full application inspection of traffic...
Page 243: ...243 Defining your security environment Controlling full application inspection of traffic...
Page 269: ...268 Limiting user access Authenticating using Out Of Band Authentication OOBA...
Page 373: ...372 Preventing attacks Enabling protection for logical network interfaces...
Page 509: ...508 Generating reports Upgrade reports...
Page 553: ...552 Advanced system settings Configuring advanced options...
Page 557: ...556 SSL server certificate management Installing a signed certificate...
Page 861: ...860 Index...






























