482
Monitoring the security gateway
Monitoring IDS/IPS alerts
Monitoring IDS/IPS alerts
When licensed, the IDS/IPS component examines all incoming packets, looking for anomalies. All
detected anomalies are logged in the security gateway’s log file. Within the log file, they are identified
as IDS/IPS alerts. You can view these alerts (if any) through the SGMI on the Monitors > Logs > IDS/IPS
Alerts tab.
All security gateway IDS/IPS alerts are sorted into general categories, called IDS/IPS event types. An
IDS/IPS event type is a short description that serves as a summarization of the type of event. IDS/IPS
event types can apply to more than one reported event, and are not necessarily unique. For example,
there may be more than one type of event classified as an FTP Generic Command Overflow event,
depending on the checks performed by the IDS/IPS component.
To help separate and uniquely identify IDS/IPS events, each event is also assigned a unique base event
type value.
The alert events that you can see in the logs are those that have been configured and applied on the
IDS/IPS Configuration tab. If you want to turn off monitoring or block traffic for a specific alert event
that has already been configured, you can do that from the IDS/IPS Alerts tab.
Prerequisites
Complete the following task before beginning this procedure:
■
■
To monitor IDS/IPS alerts
1
Create an IDS/IPS policy and configure the signatures that you want to send log messages.
2
Apply the IDS/IPS policy to an interface.
Traffic that matches IDS/IPS signatures triggers log messages as part of the security gateway log.
3
In the left pane, under Monitors, click
Logs
.
4
In the right pane, on the IDS/IPS Alerts tab, view the log messages that are IDS/IPS alerts.
5
Select an alert, and then click
Properties
.
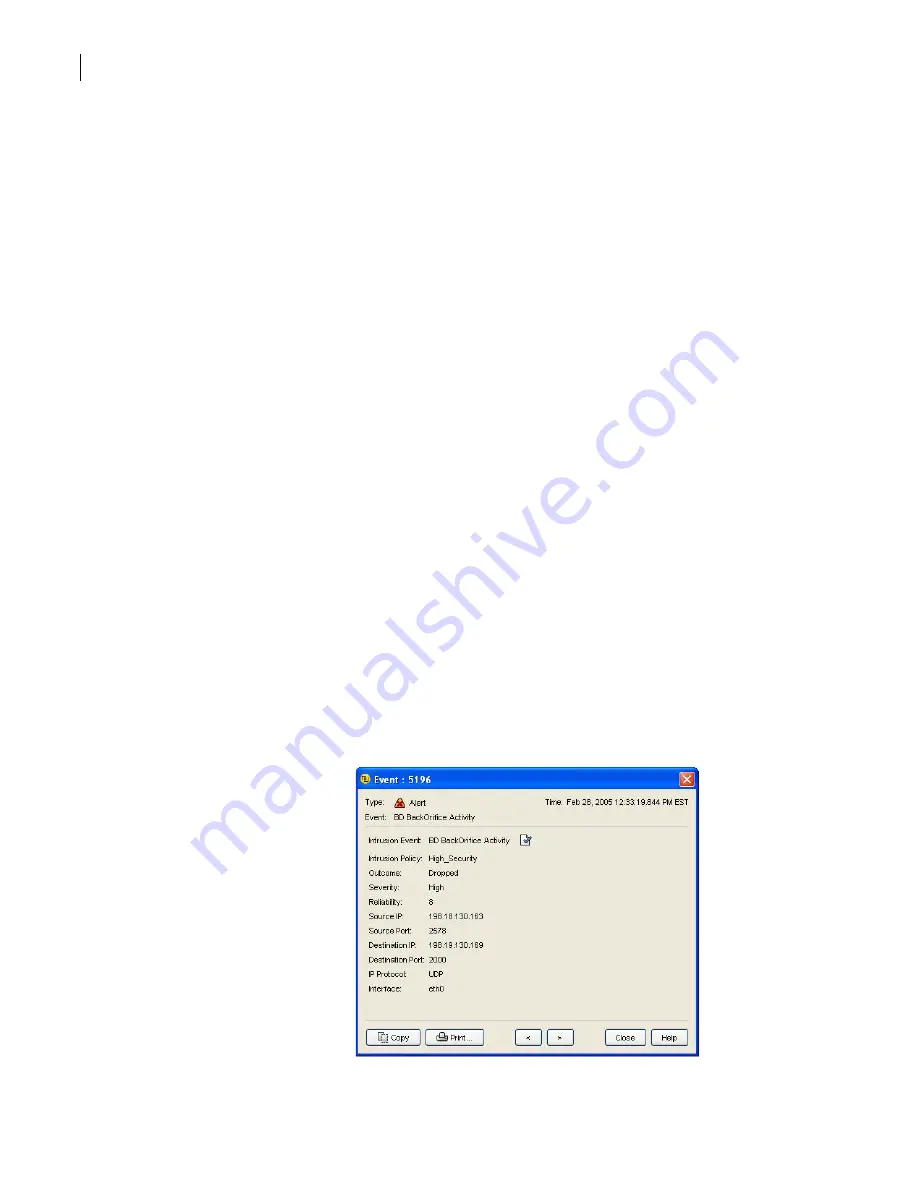
6
In the Event dialog box, view the details of the alert.
This includes the intrusion event name.
Summary of Contents for Security 5600 Series, Security 5400 Series,Clientless VPN 4400 Series
Page 76: ...76 Managing administrative access Enabling SSH for command line access to the appliance...
Page 242: ...242 Defining your security environment Controlling full application inspection of traffic...
Page 243: ...243 Defining your security environment Controlling full application inspection of traffic...
Page 269: ...268 Limiting user access Authenticating using Out Of Band Authentication OOBA...
Page 373: ...372 Preventing attacks Enabling protection for logical network interfaces...
Page 509: ...508 Generating reports Upgrade reports...
Page 553: ...552 Advanced system settings Configuring advanced options...
Page 557: ...556 SSL server certificate management Installing a signed certificate...
Page 861: ...860 Index...






























