Chapter 4
System Administration
RUGGEDCOM RSG2488
User Guide
98
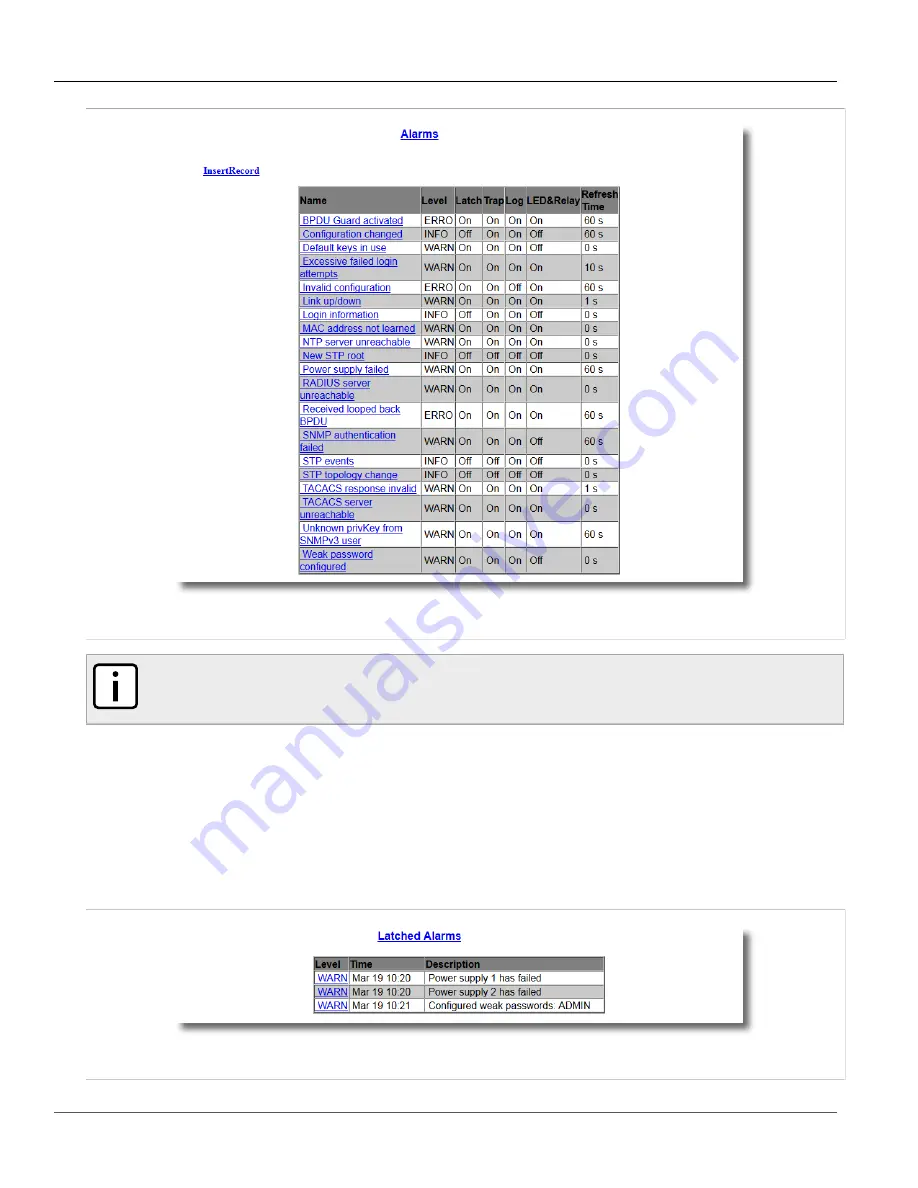
Viewing and Clearing Latched Alarms
Figure 63: Alarms Table
NOTE
This same list is accessible through the Command Line Interface (CLI) using the
alarms
. For more
Section 2.6.1, “Available CLI Commands”
For information about modifying a pre-configured alarm, refer to
Section 4.4.3, “Configuring an Alarm”
.
Section 4.4.2
Viewing and Clearing Latched Alarms
To view a list of alarms that are configured to latch, navigate to
Diagnostics > View Latched Alarms
. The
Latched
Alarms
table appears.
Figure 64: Latched Alarms Table






























