Connect Power to a PA-3400 Series Firewall
Set Up a Connecon to the Firewall
On first startup, the PA-3400 Series firewall boots into Zero Touch Provisioning (ZTP) mode by
default. ZTP mode allows you to automate the provisioning process of a new firewall that is added
to a management server. To learn more about ZTP, see
. You can also bring the
PA-3400 Series firewall online in standard mode. See the instrucons below to learn how to boot
in ZTP or standard mode.
If you have already booted up the firewall and selected the wrong mode, you must perform
a factory reset or private-data-reset before connuing.
•
Reset the Firewall to Factory Default Sengs
describes how to do a factory reset.
• To use the private-data-reset command, you must access the firewall CLI and enter the
command
request system private-data-reset
. This command will remove
all logs and restore the default configuraon.
ZTP mode is disabled if FIPS-CC mode is enabled. If the firewall boots with FIPS-CC mode
enabled, the firewall will automacally boot in standard mode.
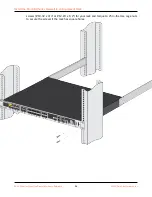
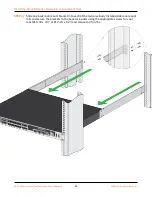
STEP 1 |
Use an RJ-45 Ethernet cable to connect the device to the correct port. The port(s) connected
will depend on which mode you intend the firewall to run in.
• (
Standard mode
) Connect the Ethernet cable from the MGT port on the firewall to the RJ-45
port of your network switch.
• (
ZTP mode
) Connect the Ethernet cable from the ZTP port (Ethernet port 1) on the firewall
to your network switch.
STEP 2 |
Confirm that the connecon to the MGT port or Ethernet port 1 has an acve network
switch.
An acve switch allows the firewall to trigger a “link up” state on the port you
connected to for your desired boot mode.
STEP 3 |
(
Standard mode only
) If you intend to boot the firewall in standard mode, you will need
access to the firewall CLI to respond to a prompt during bootup. Connect a console cable
from the PA-3400 Series firewall to your computer. Once the firewall is powered on, use a
terminal emulator such as PuTTY to access the CLI. See
PA-3400 Series Next-Gen Firewall Hardware Reference
28
©
2022 Palo Alto Networks, Inc.