DHCP Quarantine Method
Configuring NAC 800 for DHCP
10-4
Configuring NAC 800 for DHCP
The primary configuration required for using NAC 800 and DHCP is setting up
the quarantine area (see “Setting up a Quarantine Area” on page 10-4). You
should also review the following topics related to quarantining endpoints:
■
Endpoint quarantine precedence (see “Endpoint Quarantine Prece-
dence” on page 7-2).
■
Untested endpoints (see “Untestable Endpoints and DHCP Mode” on
page 7-11).
■
Unsupported operating systems (see “Defining Non-supported OS
Access Settings” on page 6-16).
■
Endpoint testing exceptions (see “Always Granting Access to an
Endpoint” on page 7-6 and “Always Quarantining an Endpoint” on
page 7-8).
■
Action to take for failed tests (see “Selecting Action Taken” on page
6-17)
■
DHCP quarantine options:
•
Router Access Control List (ACL) settings (see “Configuring the
Router ACLs” on page 10-5).
•
Static routes assigned to the endpoint (see “Adding a DHCP Quaran-
tine Area” on page 3-94)
Setting up a Quarantine Area
Set up a restricted area of your network that users can access when you do
not want to allow full access to the network. See “Quarantining, General” on
page 3-51 for instructions.
Router Configuration
If you do not elect to enforce using static routes on the endpoint (“Quarantin-
ing, General” on page 3-51), you will need to configure router ACLs.
This option restricts the network access of non-compliant endpoints by
assigning DHCP settings on a quarantined network. The network, gateway,
and ACLs restricting traffic must be configured on your router, which is
accomplished by multinetting or adding a virtual interface to the router that
acts as the quarantine gateway IP address. The quarantine area DHCP settings
must reflect this configuration on your router.
Summary of Contents for ProCurve NAC 800
Page 1: ...HP ProCurve Network Access Controller 800 Users Guide ...
Page 2: ......
Page 3: ...ProCurve Network Access Controller 800 Release 1 1 Users Guide ...
Page 43: ...2 1 2 Clusters and Servers Chapter Contents Overview 2 2 Installation Examples 2 3 ...
Page 71: ...System Configuration Management Server 3 23 Figure 3 9 System Configuration Management Server ...
Page 80: ...System Configuration User Accounts 3 32 Figure 3 12 System Configuration User Accounts ...
Page 88: ...System Configuration User Roles 3 40 Figure 3 16 System Configuration User Roles ...
Page 180: ... This page intentionally left blank ...
Page 208: ... This page intentionally left blank ...
Page 234: ...End user Access Mac OS X Endpoint Settings 5 26 Figure 5 14 Mac System Preferences ...
Page 288: ... This page intentionally left blank ...
Page 302: ... This page intentionally left blank ...
Page 306: ...High Availability and Load Balancing High Availability 8 4 Figure 8 2 DHCP Installation ...
Page 307: ...High Availability and Load Balancing High Availability 8 5 Figure 8 3 802 1X Installation ...
Page 309: ...9 1 9 Inline Quarantine Method Chapter Contents Inline 9 2 ...
Page 312: ... This page intentionally left blank ...
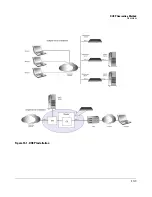
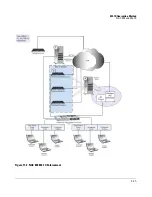
Page 315: ...DHCP Quarantine Method Overview 10 3 Figure 10 1 DHCP Installation ...
Page 318: ... This page intentionally left blank ...
Page 323: ...802 1X Quarantine Method NAC 800 and 802 1X 11 5 Figure 11 2 NAC 800 802 1X Enforcement ...
Page 324: ...802 1X Quarantine Method NAC 800 and 802 1X 11 6 Figure 11 3 802 1X Communications ...
Page 380: ... This page intentionally left blank ...
Page 418: ... This page intentionally left blank ...
Page 425: ...Reports Viewing Report Details 14 7 Figure 14 3 Test Details Report ...
Page 459: ...System Administration Creating and Replacing SSL Certificates 15 31 10 Save and exit the file ...
Page 468: ... This page intentionally left blank ...
Page 480: ... This page intentionally left blank ...
Page 526: ...Tests Help Security Settings Windows B 34 http www pcworld com article id 112138 article html ...
Page 532: ... This page intentionally left blank ...
Page 562: ... This page intentionally left blank ...