About F-Secure Corporation
F-Secure Corporation protects consumers and businesses against computer
viruses and other threats from the Internet and mobile networks. We want to
be the most reliable provider of security services in the market. One way to
demonstrate this is the speed of our response. According to independent
studies in 2004, 2005 and 2006 our response time to new threats is
significantly faster than our major competitors. Our award-winning solutions
are available for workstations, gateways, servers and mobile phones. They
include antivirus and desktop firewall with intrusion prevention, antispam and
antispyware solutions. Founded in 1988, F-Secure has been listed on the
Helsinki Exchanges since 1999, and has been consistently growing faster
than all its publicly listed competitors. F-Secure headquarters are in Helsinki,
Finland, and we have regional offices around the world. F-Secure protection
is also available as a service through major ISPs, such as Deutsche Telekom,
France Telecom, PCCW and Charter Communications. F-Secure is the global
market leader in mobile phone protection provided through mobile operators,
such as T-Mobile and Swisscom and mobile handset manufacturers such as
Nokia. The latest real-time virus threat scenario news are available at the
F-Secure Data Security Lab weblog at
http://www.f-secure.com/weblog/
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
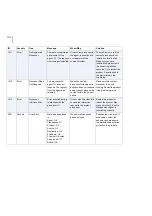
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
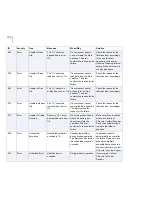
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
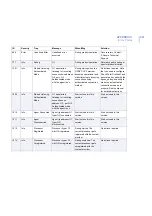
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
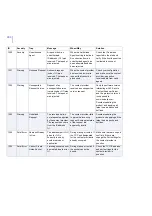
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...