58
3.9
Upgrading from Previous Product Versions
To upgrade from the product version 7.10 or 8.0, follow the standard
installation instructions.
To upgrade from the product version 6.62, follow instructions described in
this section.
Backup your current configuration before starting the upgrade.
Standalone
Mode
1.
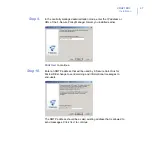
Install F-Secure Anti-Virus for Microsoft Exchange. For more
information, see “
Installing F-Secure Anti-Virus for Microsoft
•
Your previous settings are migrated to the new version during the
installation.
•
You may need to reboot the system to complete the installation.
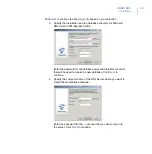
2.
After the installation, open F-Secure Anti-Virus for Microsoft
Exchange Web Console and check the policy migration report. The
link to the report is in the
Getting Started
page.
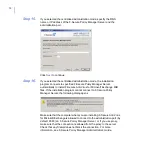
3.
Check the product configuration to finish the upgrade.
Centralized
Administration
Mode
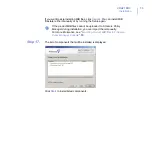
Before you install the latest version of the product, upgrade F-Secure
Policy Manager to version 9.0 or later.
IMPORTANT: F-Secure Anti-Virus for Microsoft Exchange 9.0
does not support Microsoft Exchange Server 2000 nor Microsoft
Windows Server 2000. You cannot upgrade the product that is
running on those platforms.
We recommend that you upgrade your Microsoft SQL Server to the
latest version. If you are using MSDE, upgrade it to Microsoft SQL
Server 2005 Express Edition.
The report file is located on the local disk in:
%Program Files%\F-Secure\Anti-Virus Agent for Microsoft
Exchange\msemigrpt.htm.
We recommend that you back up your policy data (select Save
Policy As in the Policy Manager Console) before the upgrade.
Summary of Contents for ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00
Page 1: ...F Secure Anti Virus for Microsoft Exchange Deployment Guide...
Page 6: ...4 ABOUT THIS GUIDE How This Guide Is Organized 5 Conventions Used in F Secure Guides 6...
Page 19: ...17 2 DEPLOYMENT Installation Modes 18 Network Requirements 19 Deployment Scenarios 20...
Page 64: ...62 4 CONFIGURING F SECURE SPAM CONTROL Overview 63 Realtime Blackhole List Configuration 64...
Page 106: ...104 B APPENDIX Services and Processes List of Services and Processes 105...
Page 115: ......