100
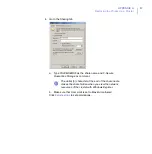
3.
Distribute the policy.
4.
All nodes receive new settings next time they poll the F-Secure Policy
Manager Server.
If you need to change settings on a particular node, follow these
instructions:
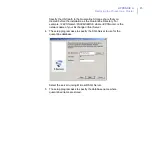
1.
Select the corresponding host in the Policy Domains.
2.
Change required settings.
3.
Distribute the policy.
4.
All nodes will receive new settings the next time they poll F-Secure
Policy Manager Server.
A.5
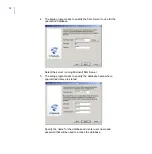
Using the Quarantine in the Cluster Installation
You can manage quarantined items with the Web Console by connecting
to any node of the cluster.
You can release, reprocess and download quarantined messages and
attachments when at least one node of the cluster is currently online.
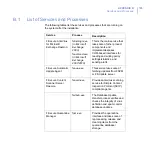
Configuring
Mailbox Role
Servers
However, as the clustered Exchange 2007 can have the mailbox role only
and not all members of Exchange 2010 Database Availability Group may
have Hub Transport Role, you need to configure the hub transport role
and mailbox role servers so that quarantined messages can be delivered:
Hub Transport Role Server:
1.
Share the
Pickup
folder on the Exchange Hub Server. By default, the
Pickup
folder is located at
%Program Files%\Microsoft\Exchange
Server\TransportRoles\Pickup
.
Use the default name (Pickup) for the share so that it can be
accessed at
\\HubServerName\Pickup
.
You need to configure F-Secure Anti-Virus for Microsoft Exchange
Web Console to accept connections from authorized hosts. By
default, the Web Console accepts connections from the local host
only.
Summary of Contents for ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00
Page 1: ...F Secure Anti Virus for Microsoft Exchange Deployment Guide...
Page 6: ...4 ABOUT THIS GUIDE How This Guide Is Organized 5 Conventions Used in F Secure Guides 6...
Page 19: ...17 2 DEPLOYMENT Installation Modes 18 Network Requirements 19 Deployment Scenarios 20...
Page 64: ...62 4 CONFIGURING F SECURE SPAM CONTROL Overview 63 Realtime Blackhole List Configuration 64...
Page 106: ...104 B APPENDIX Services and Processes List of Services and Processes 105...
Page 115: ......