User’s Manual
287
5.19.3.3
Anti-Dos Attack
You can enable SYN Flood Attack Defense and ICMP Flood Attack Defense to defend the device
against Dos attack.
5.19.3.4
Sync Time-Allowlist
The synchronization is only allowed with hosts in the trusted list.
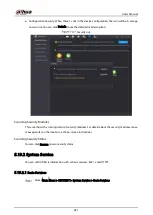
Step 1
Select Main Menu > SECURITY > Attack Defense > Sync Time-Allowlist.
Step 2
Select Enable to enable Sync Time-Allowlist function.
Step 3
Configure the parameters.
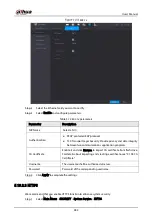
Table 5-77
Allowlist parameters
Parameter
Description
Add
You can add trusted hosts for time synchronization.
Type
Select IP address or IP segment for hosts to be added.
IP Address
Input the IP address of a trusted host.
When Type is IP Address, it can be configured
Start Address
Input the start IP address of trusted hosts.
When Type is IP Segment, it can be configured
End Address
Input the end IP address of trusted hosts.
When Type is IP Segment, it can be configured
Step 4
Click Apply to complete the settings.
5.19.4
CA Certificate
You can create or import device certificate and install trusted CA Certificate.
5.19.4.1
Device Certificate
Create Certificate
Select Main Menu > SECURITY > CA Certificate > Device Certificate.
Summary of Contents for XVR Series
Page 1: ...Digital Video Recorder User s Manual V1 5 0 ZHEJIANG DAHUA VISION TECHNOLOGY CO LTD...
Page 20: ...User s Manual 8 Fix HDD Connect cables Install the bracket and then fasten the screws...
Page 115: ...User s Manual 103 Main menu...
Page 201: ...User s Manual 189 Search result diagram Search result list...
Page 221: ...User s Manual 209 Search results diagram Search results list Double click the video or click...
Page 240: ...User s Manual 228 List For the data displayed in graph see Figure 5 187 Graph...
Page 283: ...User s Manual 271 Main stream Sub stream...
Page 327: ...User s Manual 315 Login Click Forgot Password Reset password Click OK...
Page 357: ...User s Manual 345 Neutral cable...
Page 363: ...User s Manual...