Appendix B: IDP Signature Groups
For IDP scanning, the following signature groups are available for selection. These groups are
only available for the D-Link Advanced IDP Service. There is a version of each group under the
three
Types
of IDS, IPS and Policy. For further information see
Section 6.6, “Intrusion Detection
.
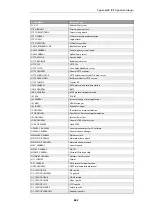
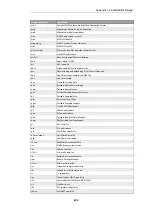
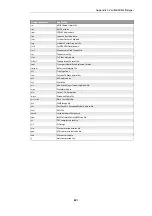
Group Name
Intrusion Type
APP_AMANDA
Amanda, a popular backup software
APP_ETHEREAL
Ethereal
APP_ITUNES
Apple iTunes player
APP_REALPLAYER
Media player from RealNetworks
APP_REALSERVER
RealNetworks RealServer player
APP_WINAMP
WinAMP
APP_WMP
MS Windows Media Player
AUTHENTICATION_GENERAL
Authenticantion
AUTHENTICATION_KERBEROS
Kerberos
AUTHENTICATION_XTACACS
XTACACS
BACKUP_ARKEIA
Network backup solution
BACKUP_BRIGHTSTOR
Backup solutions from CA
BACKUP_GENERAL
General backup solutions
BACKUP_NETVAULT
NetVault Backup solution
BACKUP_VERITAS
Backup solutions
BOT_GENERAL
Activities related to bots, including those controlled by IRC channels
BROWSER_FIREFOX
Mozilla Firefox
BROWSER_GENERAL
General attacks targeting web browsers/clients
BROWSER_IE
Microsoft IE
BROWSER_MOZILLA
Mozilla Browser
COMPONENT_ENCODER
Encoders, as part of an attack.
COMPONENT_INFECTION
Infection, as part of an attack
COMPONENT_SHELLCODE
Shell code, as part of the attacks
DB_GENERAL
Database systems
DB_MSSQL
MS SQL Server
DB_MYSQL
MySQL DBMS
DB_ORACLE
Oracle DBMS
DB_SYBASE
Sybase server
DCOM_GENERAL
MS DCOM
DHCP_CLIENT
DHCP Client related activities
DHCP_GENERAL
DHCP protocol
DHCP_SERVER
DHCP Server related activities
DNS_EXPLOIT
DNS attacks
DNS_GENERAL
Domain Name Systems
DNS_OVERFLOW
DNS overflow attack
DNS_QUERY
Query related attacks
ECHO_GENERAL
Echo protocol and implementations
ECHO_OVERFLOW
Echo buffer overflow
FINGER_BACKDOOR
Finger backdoor
FINGER_GENERAL
Finger protocol and implementation
FINGER_OVERFLOW
Overflow for Finger protocol/implementation
884
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...