9-29
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 9 Network Address Translation (NAT)
Static NAT
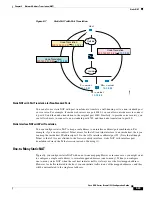
Figure 9-7
Static NAT with Port Translation
Static NAT with Port Translation for Non-Standard Ports
You can also use static NAT with port translation to translate a well-known port to a non-standard port
or vice versa. For example, if inside web servers use port 8080, you can allow outside users to connect
to port 80, and then undo translation to the original port 8080. Similarly, to provide extra security, you
can tell web users to connect to non-standard port 6785, and then undo translation to port 80.
Static Interface NAT with Port Translation
You can configure static NAT to map a real address to an interface address/port combination. For
example, if you want to redirect Telnet access for the ASA outside interface to an inside host, then you
can map the inside host IP address/port 23 to the ASA interface address/port 23. (Note that although
Telnet to the ASA is not allowed to the lowest security interface, static NAT with interface port
translation redirects the Telnet session instead of denying it).
One-to-Many Static NAT
Typically, you configure static NAT with a one-to-one mapping. However, in some cases, you might want
to configure a single real address to several mapped addresses (one-to-many). When you configure
one-to-many static NAT, when the real host initiates traffic, it always uses the first mapped address.
However, for traffic initiated to the host, you can initiate traffic to any of the mapped addresses, and they
will be untranslated to the single real address.
Ho
s
t
O
u
t
s
ide
In
s
ide
Undo Tr
a
n
s
l
a
tion
10.1.2.27
209.165.201.3:21
Undo Tr
a
n
s
l
a
tion
10.1.2.28
209.165.201.3:80
Undo Tr
a
n
s
l
a
tion
10.1.2.29
209.165.201.3:25
FTP
s
erver
10.1.2.27
HTTP
s
erver
10.1.2.28
S
MTP
s
erver
10.1.2.29
130031
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......