9-28
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 9 Network Address Translation (NAT)
Static NAT
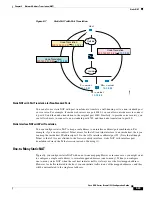
The following figure shows a typical static NAT with port translation scenario showing both a port that
is mapped to itself and a port that is mapped to a different value; the IP address is mapped to a different
value in both cases. The translation is always active so both translated and remote hosts can initiate
connections.
Figure 9-6
Typical Static NAT with Port Translation Scenario
Note
For applications that require application inspection for secondary channels (for example, FTP and VoIP),
the ASA automatically translates the secondary ports.
Static NAT with Identity Port Translation
The following static NAT with port translation example provides a single address for remote users to
access FTP, HTTP, and SMTP. These servers are actually different devices on the real network, but for
each server, you can specify static NAT with port translation rules that use the same mapped IP address,
but different ports. For details on how to configure this example, see
Single Address for FTP, HTTP, and
SMTP (Static NAT-with-Port-Translation), page 10-5
10.1.1.1:23
209.165.201.1:23
In
s
ide
O
u
t
s
ide
10.1.1.2:8080
209.165.201.2:80
130044
S
ec
u
rity
Appli
a
nce
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......