© Copyright 2007 Cisco Systems, Inc.
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
22
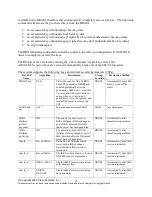
IKE session
encrypt key
TRIPLE-
DES/AES
The IKE session encrypt key.
DRAM
Automatically after IKE
session terminated.
IKE session
authentication
key
HMAC-SHA-1
The IKE session authentication
key.
DRAM
Automatically after IKE
session terminated.
ISAKMP
preshared
Shared secret
The key used to generate IKE
skeyid during preshared-key
authentication. “no crypto isakmp
key” command zeroizes it. This key
can have two forms based on
whether the key is related to the
hostname or the IP address.
NVRAM
“# no crypto isakmp
key”
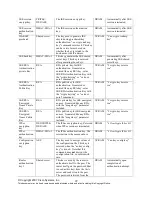
IKE hash key
HMAC-SHA-1
This key generates the IKE shared
secret keys. This key is zeroized
after generating those keys.
DRAM
Automatically after
generating IKE shared
secret keys.
IKE RSA
Authentication
private Key
RSA
RSA private key for IKE
authentication. Generated or
entered like any RSA key, set as
IKE RSA Authentication Key with
the “crypto keyring” or “ca trust-
point” command.
NVRAM
“# crypto key zeroize
rsa"
IKE RSA
Authentication
Public Key
RSA
RSA public key for IKE
authentication. Generated or
entered like any RSA key, set as
IKE RSA Authentication Key with
the “crypto keyring” or “ca trust-
point” command.
NVRAM
“# crypto key zeroize
rsa"
IKE RSA
Encrypted
Nonce Private
Key
RSA
RSA private key for IKE encrypted
nonces. Generated like any RSA,
with the “usage-keys” parameter
included.
NVRAM
“# crypto key zeroize
rsa"
IKE RSA
Encrypted
Nonce Public
Key
RSA
RSA public key for IKE encrypted
nonces. Generated like any RSA,
with the “usage-keys” parameter
included.
NVRAM
“# crypto key zeroize
rsa"
IPSec
encryption
key
DES/TRIPLE-
DES/AES
The IPSec encryption key. Zeroized
when IPSec session is terminated.
DRAM
“# Clear Crypto IPSec SA”
IPSec
authentication
key
HMAC-SHA-1
The IPSec authentication key. The
zeroization is the same as above.
DRAM
“# Clear Crypto IPSec SA”
Configuration
encryption
key
AES
The key used to encrypt values of
the configuration file. This key is
zeroized when the “no key config-
key” is issued. Note that this
command does not decrypt the
configuration file, so zeroize with
care.
NVRAM
“# no key config-key”
Router
authentication
key 1
Shared secret
This key is used by the router to
authenticate itself to the peer. The
router itself gets the password (that
is used as this key) from the AAA
server and sends it onto the peer.
The password retrieved from the
DRAM
Automatically upon
completion of
authentication attempt.