7.17 Uploading a Configuration
51
and should not be changed. This value has been chosen to provide an extremely low likelihood of
false detection, while having very high sensitivity to a real attack.
Enable Re-Locking
If disabled (unchecked) the clock will never attempt to recover from a spoofing detection. Normally,
if ”Enable Re-locking” is checked and the clock sees the spoofing attack terminate, it will attempt
to re-lock and clear the ”alarm.”
Attempt to Re-lock After
As the name suggests this feature terminates the spoofing features after a specific period of time
(in seconds) has elapsed, regardless of the detection state. Requires the Enable Re-locking setting
be enabled.
For more information on clock’s security, see Section 7.3.
7.17
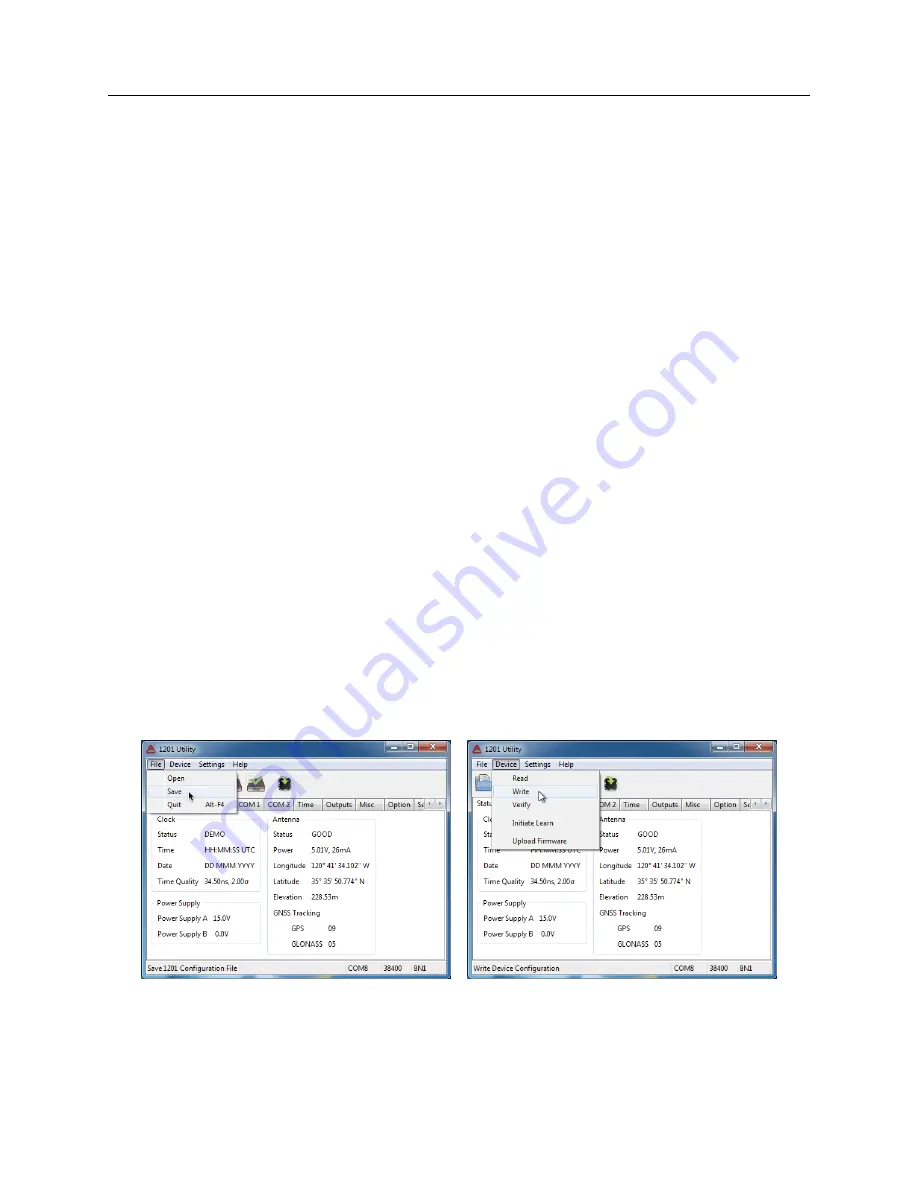
Uploading a Configuration
The Utility allows you to save a configuration file from one clock and upload the saved file to other
clocks. To do this,
1. Start the Utility and connect to the originating clock. Make sure you have chosen the correct
COM port number and baud rate.
2. Select Device
>
Read, or click the Read icon, to download the configuration.
3. Select File
>
Save to save a copy of the downloaded configuration.
4. Connect the serial cable, and possibly USB-to-serial adapter, to the new clock. Make sure
that the COM port and baud rate settings are correct on the second clock.
5. Select Device
>
Write, or click the Write icon, to upload the saved configuration to the new
clock.
6. Select Device
>
Verify, or click the Verify icon, to verify that the upload matches the
configuration file.
Figure 7.20: Uploading a Configuration File to another clock






























